Payroll Fraud Alert: Direct Deposit Scam

Recently, there has been a significant increase in the number of employers across the country who have been targeted by payroll fraudsters. Scammers continue to get more resourceful, cunning and technically savvy in their attempts to defraud victims by gaining access to financial accounts as well as valuable personal information.
Here is an outline of the most recent scheme and some tips on how to prevent your company and employees from falling victim to the perpetrators.
DIRECT DEPOSIT CHANGE REQUEST:
The owner or the person who is responsible for HR and/or processing payroll receives an email communication that seems to come from one of their staff. The email requests information on how to make a change to their direct deposit account and typically implies some sense of urgency. Typically, the sender seeks to inactivate the old direct deposit account and replace it with a completely new account. Here is an example of an email request along with some key identifiers to look for that are red flags for phishing and other fraudulent email scams:
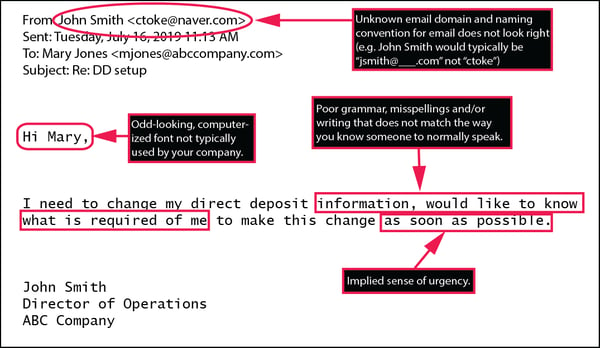
In most cases, employers act on good faith to complete what seems to be a legitimate request. It is only discovered after the fact that the email did not actually come from an employee, but rather came from someone who is trying to engage in a scam to divert fund. In some cases this may be only be brought to light after the employee misses one or two payroll payments, potentially causing financial distress and late penalties for the employee. The success rate that hackers are experiencing with this type of threat is very high – high enough to compel them to continue getting more and more clever.
Here are some steps you can implement to protect yourself and your employees from this type of fraudulent activity:
- Verify with the requesting employee that they submitted the request either by phone or by emailing them directly using their company email address.
- Print a hardcopy of the email and copy of a direct deposit form for the employee and deliver to him/her by hand or possibly through inter-office mail. For a sample of our direct deposit form, CLICK HERE.
- ALWAYS require a voided original check with banking information along with a completed direct deposit form before making changes.
- Consider utilizing the Employee Self Service functionality within CheckmateHCM’s payroll software to allow employees to make Direct Deposit updates themselves.
- Review your policy for publishing email addresses and contact information for personnel on your website as this provides prospective thieves with easy access to information to pose as a legitimate employee and perpetuate their scheme.
Should you receive this type of email, we recommend following your standard internal security protocols such as forwarding a copy of the email to your IT Department and alerting others within your organization to be alert for similar fake inquiries.
Guidance from the IRS
The IRS has termed these types of scams as Business Email Compromise (BEC) / Business Email Spoofing (BES). They closely monitor and investigate these and other attempted fraudulent activity and request that anyone receiving these emails forward copies to their appropriate investigative branches.
Where to send the BEC/BES emails
General non-tax related BEC/BES email scams should be forwarded to Internet Crime Complaint Center (IC3), which is monitored by the Federal Bureau of Investigation. The public can file a complaint about email scams or other internet-related scams by going to www.ic3.gov.
Tax professionals and others should also report tax-related phishing emails to phishing@irs.gov. This account is monitored by IRS cybersecurity professionals. This reporting process also enables the IRS and Security Summit partners to identify trends and issue warnings.
Interested in implementing a solution that can increase your employees’ data security, help your company avoid manual payroll errors and streamline processes electronically to save your HR and management team time spent performing time-consuming and risk-prone paperwork administration?

